by Con Mallon, CrowdStrike | Negosentro.com |
Ransomware offers a lucrative market for cybercriminals — as noted by Tech Republic, ransomware threats cost businesses more than $1 billion last year. While large enterprises and government agencies remain high-priority targets, small businesses and individual users are also under threat. For hackers, this is a growth industry: Personal and SMB applications often come with minimal IT security, making compromise easier and victims more likely to pay. More worrisome is the fact malicious actors are leveraging these targets to test new iterations of ransomware attacks.
Fork It Over
Ransomware works on a simple principle: Attackers hold critical files hostage, then demand that users pay or see their data deleted. For small businesses this might be financial records or customer data sheets, while personal users could find family photos or tax information encrypted. Typically, hackers make a ransom demand in Bitcoin — an untraceable, secure digital currency — often ranging between $500 and $2,000. Without the benefit of enterprise-level IT departments, many SMBs and individual users aren’t sure how to defeat ransomware threats, leading them to pay — and hope that hackers are as good as their word.
Thankfully, security companies are getting better at cracking ransomware code and publishing their solution online. The downside is hackers have taken this as a challenge and created a new attack vector: fileless ransomware.
Infection Interaction
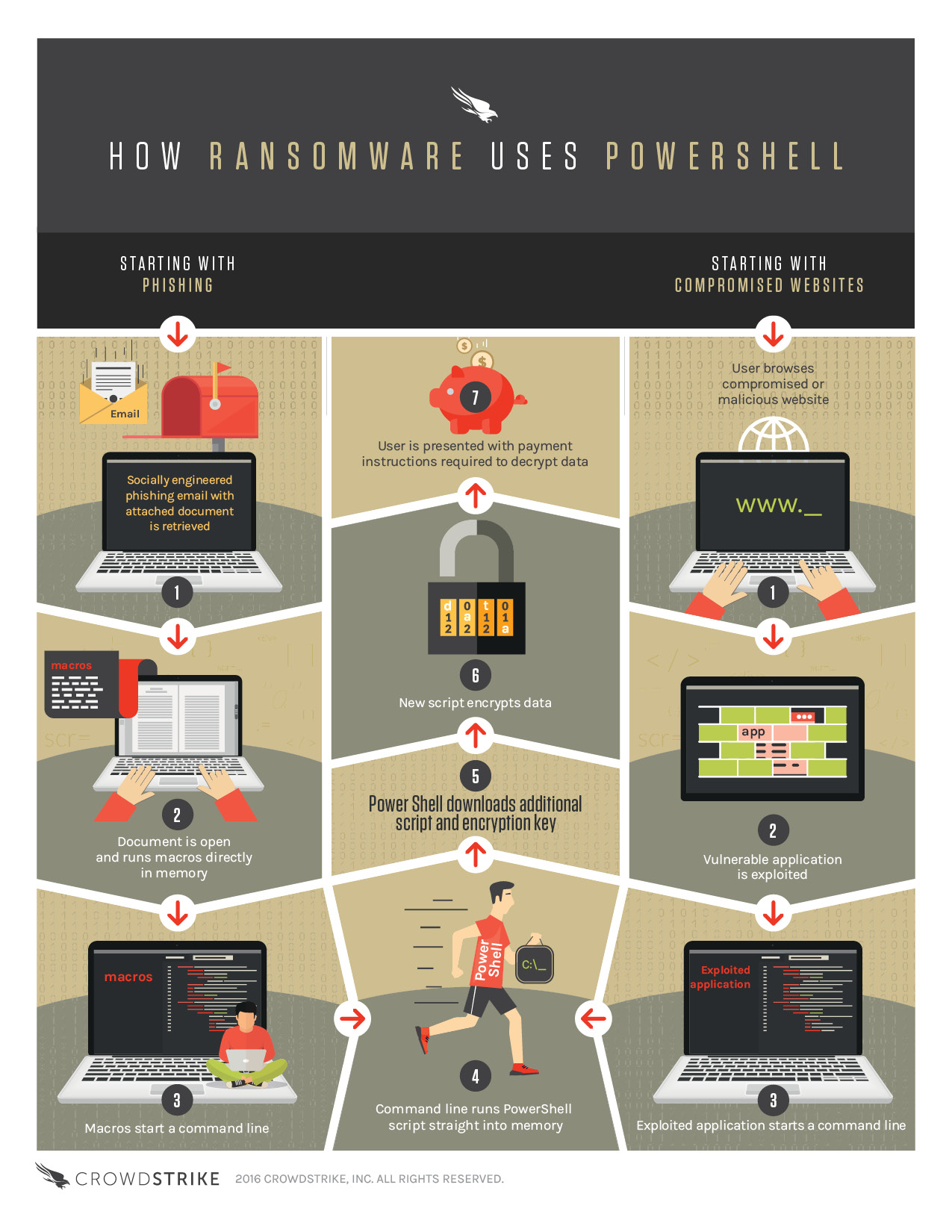
Basic ransomware infections are straightforward — users are tricked into downloading an attachment via email or through a compromised Web link. These malicious files then contact a command and control (C&C) center, which sends the ransomware package itself to encrypt data and display a ransom message.
Fileless malware differs by using Word macros in downloaded documents or compromised Web apps to start a command line, which in turn runs PowerShell scripts straight into device memory. Since PowerShell is an approved and trusted application on most systems, these scripts aren’t flagged as potentially harmful. Hackers use these scripts to download their encryption key, lock files and demand payment — all while antivirus and local security measures are left in the dark.
Bottom line? Ransomware casts a wide net. Keep your business and personal files safe; see the accompanying infographic to learn more about existing malware threats and the rise of fileless infection techniques.
How Ransomware Uses Powershell from CrowdStrike
—
Author bio: Con Mallon is Senior Director of Product Marketing at CrowdStrike, responsible for product positioning and messaging, go-to-market programs, competitive differentiation, and sales assets and tools. Con started his career in the United Kingdom, and has more than 20 years of marketing and product management experience within the technology sector.